We share the latest updated CompTIA SY0-601 test questions and answers for free, all test questions are real cracked, guaranteed to be true and effective!
You can practice the test online! Or download the latest SY0-601 exam pdf. The free exam questions are only part of what we share. If you want to get the complete CompTIA SY0-601 exam questions and answers, you can get them in leads4pass. The leads4pass SY0-601 exam dumps contain VCE dumps and PDF dumps.
CompTIA SY0-601 Exam “CompTIA Security+ 2021” https://www.leads4pass.com/sy0-601.html (Total Questions: 417 Q&A)
Download the CompTIA SY0-601 exam pdf for free
Free share CompTIA SY0-601 exam PDF from Google Drive provided by leads4pass
https://drive.google.com/file/d/1TkG4_k1sNDRwDR2x5XXVZcBoAqU-u5hF/
Real questions CompTIA SY0-601 exam questions practice test
QUESTION 1
HOTSPOT
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS Please click on the below items on the network diagram and configure them accordingly:
1. WAP
2. DHCP Server
3. AAA Server
4. Wireless Controller
5. LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
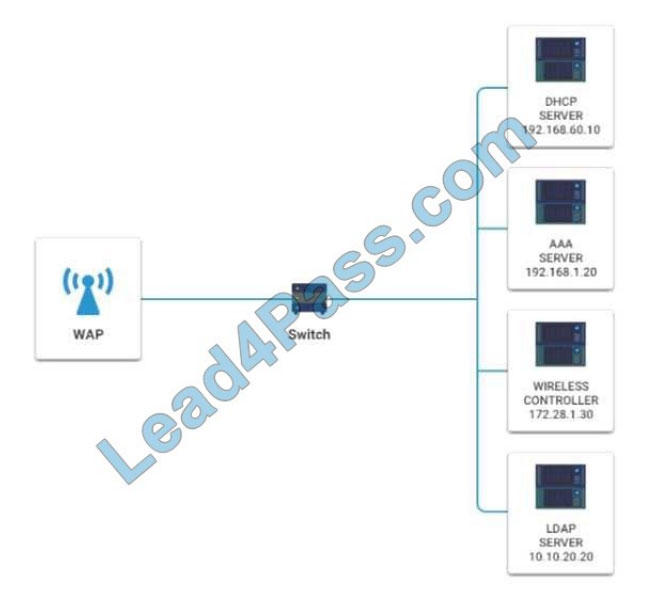
Hot Area:
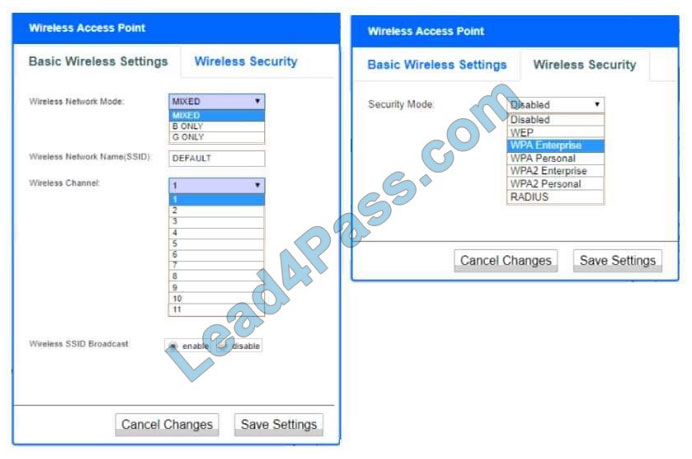
Correct Answer:
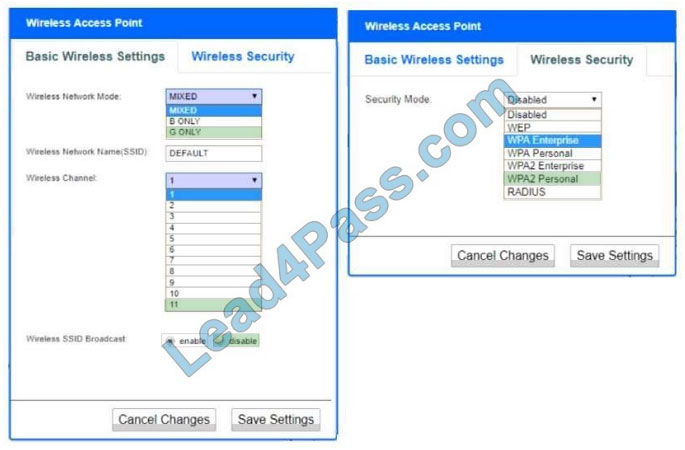
Wireless Access Point:
1. Network Mode – G only
2. Wireless Channel – 11
3. Wireless SSID Broadcast – disable
4. Security settings – WPA2 Personal
QUESTION 2
A company has decided to move its operations to the cloud. It wants to utilize technology that will prevent users from
downloading company applications for personal use, restrict data that is uploaded, and have visibility into which
applications are being used across the company. Which of the following solutions will BEST meet these requirements?
A. An NGFW
B. A CASB
C. Application whitelisting
D. An NG-SWG
Correct Answer: B
QUESTION 3
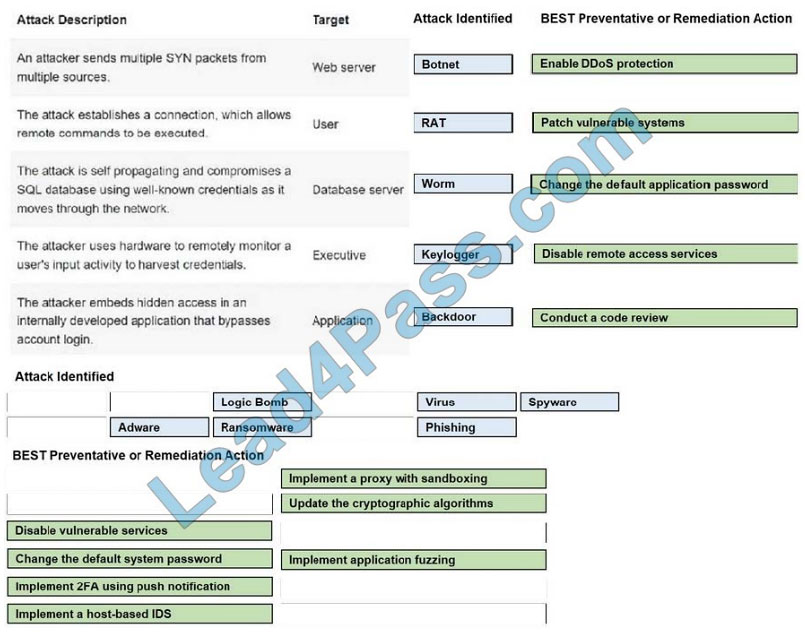
HOTSPOT
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its
remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the
simulation, please click the Reset All button.
Select and Place: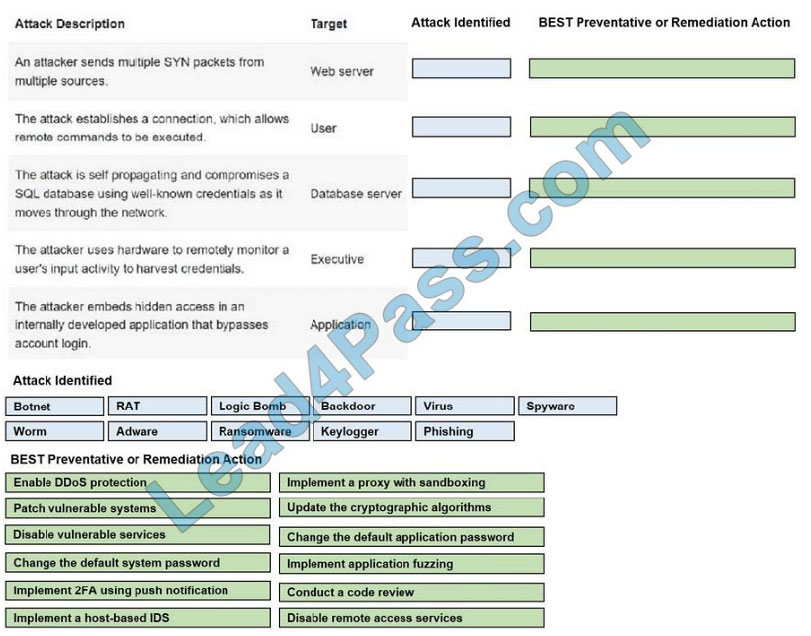
Correct Answer:
QUESTION 4
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has only been given the documentation available to the customers of the applications. Which of the following BEST
represents the type of testing that will occur?
A. Bug bounty
B. Black-box
C. Gray-box
D. White-box
Correct Answer: A
QUESTION 5
DRAG DROP
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the
appropriate control used to accomplish the account management goal. Options may be used once or not at all.
Select and Place: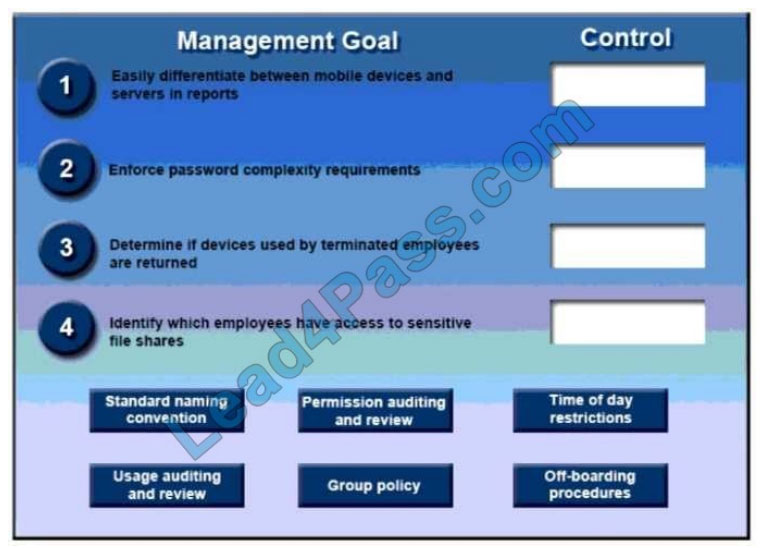
Correct Answer:
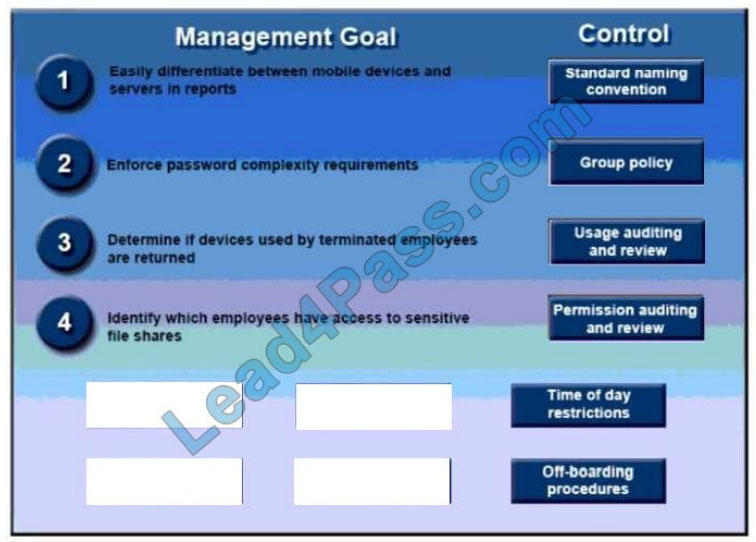
QUESTION 6
A security administrator discovers that an attack has been completed against a node on the corporate network. All
available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been
compromised and drag and drop the appropriate actions to complete the incident response on the network. The
environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incident responses.
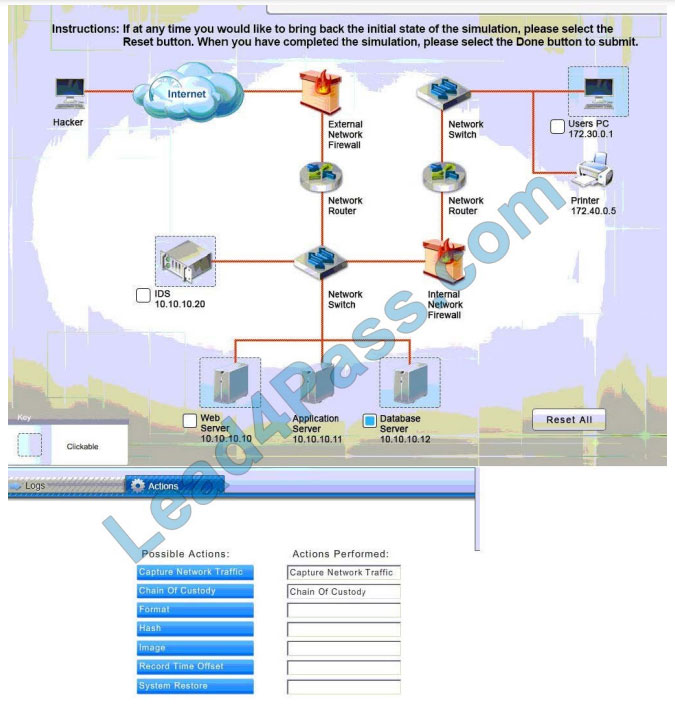
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have
been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at anytime you would like to bring back the initial state of the
simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
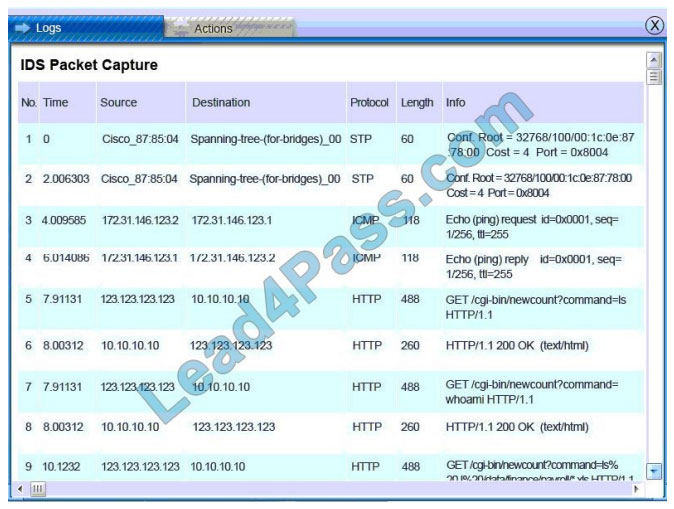
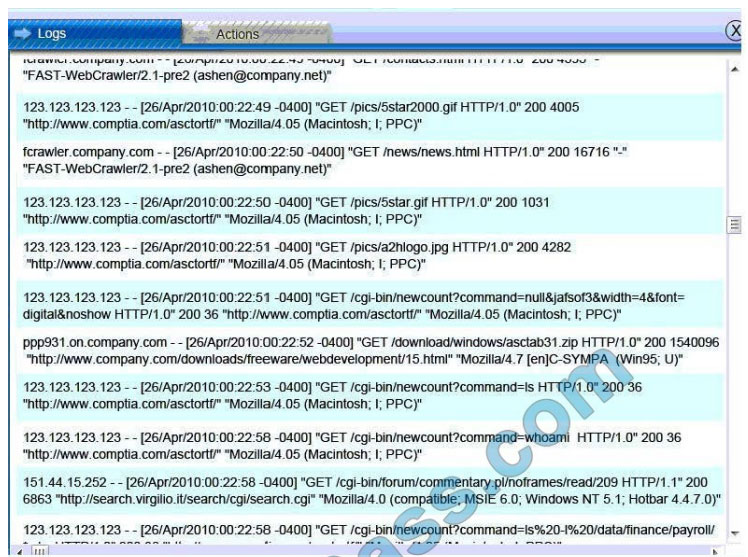
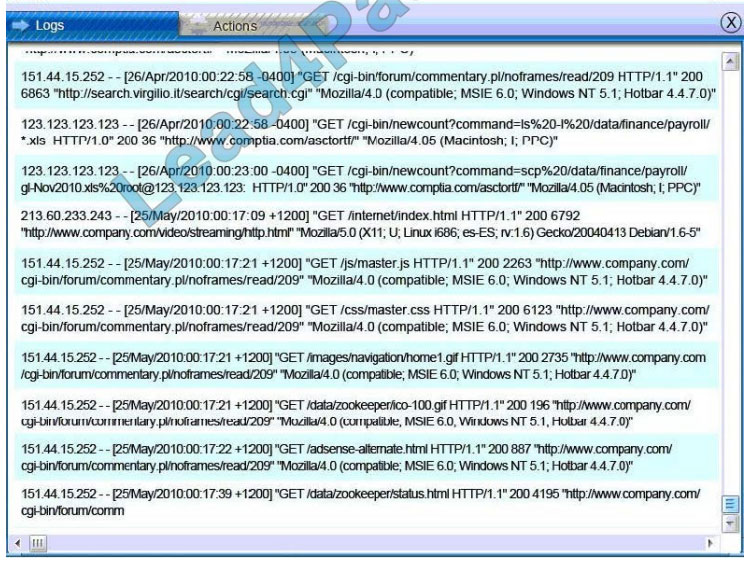
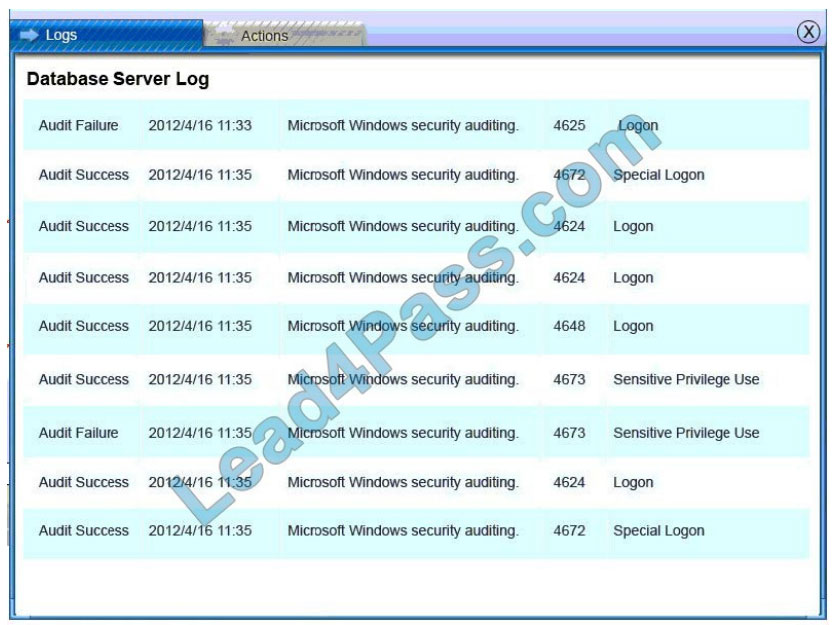
Database server was attacked; actions should be to capture network traffic and Chain of Custody.
(The database server logs shows the Audit Failure and Audit Success attempts)It is only logical that all the logs will be
stored on the database server and the least disruption action on the network to take as a response to the incident would be to check the logs (since these are already collected and stored) and maintain a chain of custody of those logs.
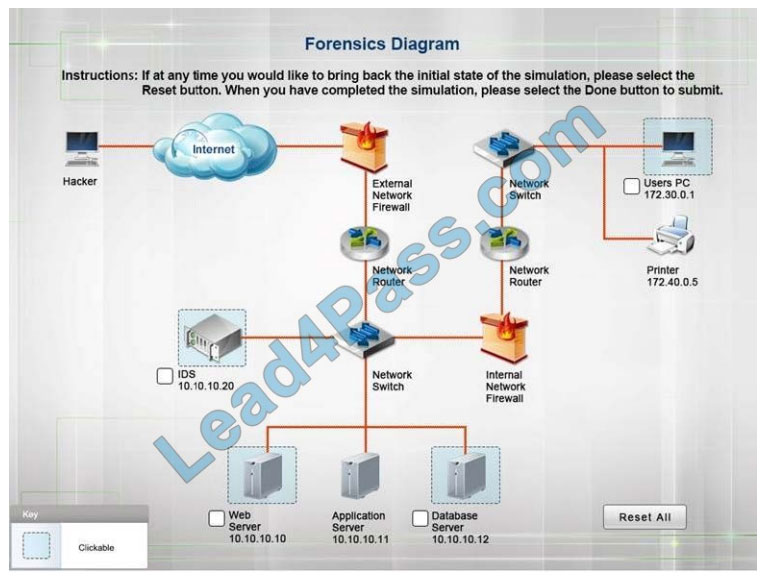
Correct Answer:
IDS Server Log:
Web Server Log: Database Server Log:
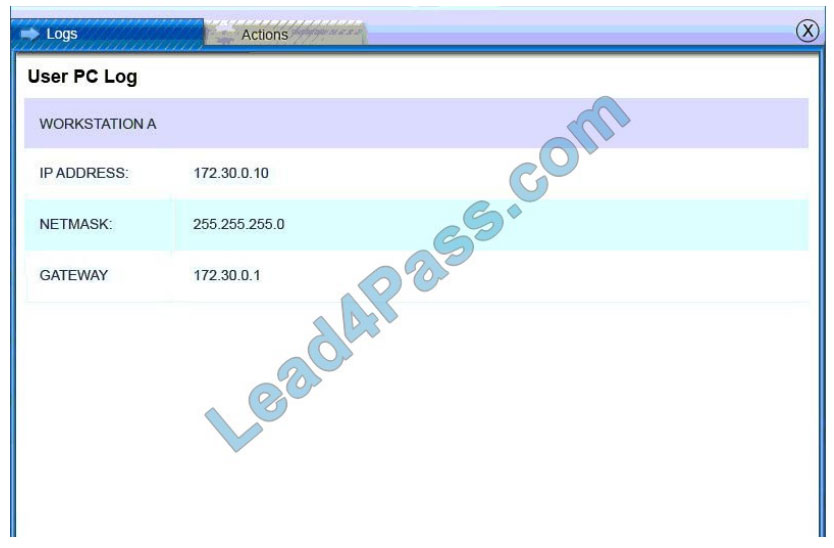
Users PC Log:
QUESTION 7
After entering a username and password, and administrator must gesture on a touch screen. Which of the following
demonstrates what the administrator is providing?
A. Multifactor authentication
B. Something you can do
C. Biometric
D. Two-factor authentication
Correct Answer: D
QUESTION 8
Which of the following should a data owner require all personnel to sign to legally protect intellectual property?
A. An NDA
B. An AUP
C. An ISA
D. An MOU
Correct Answer: D
QUESTION 9
A commercial cyber-threat intelligence organization observes IoCs across a variety of unrelated customers. Prior to
releasing specific threat intelligence to other paid subscribers, the organization is MOST likely obligated by contracts to:
A. perform attribution to specific APTs and nation-state actors.
B. anonymize any PII that is observed within the IoC data.
C. add metadata to track the utilization of threat intelligence reports.
D. assist companies with impact assessments based on the observed data.
Correct Answer: B
QUESTION 10
Accompany deployed a WiFi access point in a public area and wants to harden the configuration to make it more
secure. After performing an assessment, an analyst identifies that the access point is configured to use WPA3, AES,
WPS, and RADIUS.
Which of the following should the analyst disable to enhance the access point security?
A. WPA3
B. AES
C. RADIUS
D. WPS
Correct Answer: D
QUESTION 11
Drag and drop the correct protocol to its default port.
Select and Place: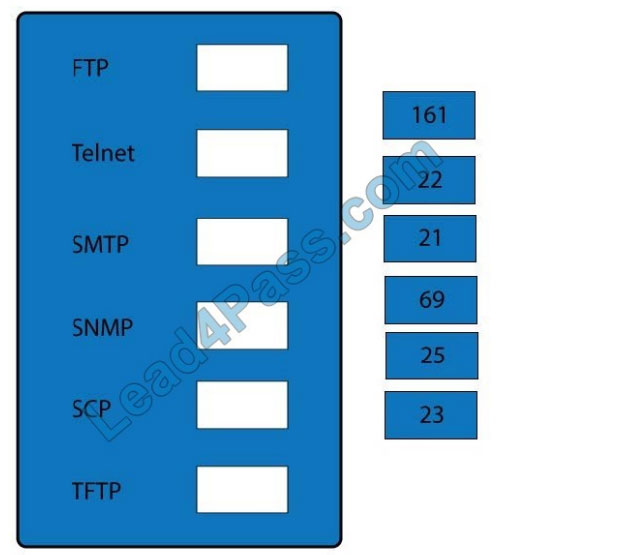
Correct Answer:
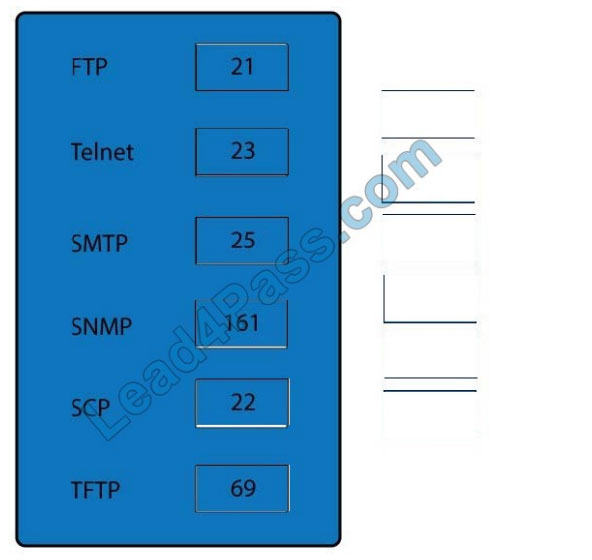
FTP uses TCP port 21.
Telnet uses port 23.
SSH uses TCP port 22. All protocols encrypted by SSH, including SFTP, SHTTP, SCP, SExec, and slogin, also use
TCP port 22. Secure Copy Protocol (SCP) is a secure filetransfer facility based on SSH and Remote Copy Protocol
(RCP).
Secure FTP (SFTP) is a secured alternative to standard File Transfer Protocol (FTP).
SMTP uses TCP port 25.
Port 69 is used by TFTP.
SNMP makes use of UDP ports 161 and 162.
References:
Stewart, James Michael, CompTIA Security+ Review Guide, Sybex, Indianapolis, 2014, pp. 42, 45, 51
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
QUESTION 12
An analyst is trying to identify insecure services that are running on the internal network After performing a port scan the analyst identifies that a server has some insecure services enabled on default ports Which of the following BEST
describes the services that are currently running and the secure alternatives for replacing them\\’ (Select THREE)
A. SFTP FTPS
B. SNMPv2 SNMPv3
C. HTTP, HTTPS
D. TFTP FTP
E. SNMPv1, SNMPv2
F. Telnet SSH
G. TLS, SSL
H. POP, IMAP
I. Login, rlogin
Correct Answer: BCF
QUESTION 13
A user recently attended an exposition and received some digital promotional materials The user later noticed blue
boxes popping up and disappearing on the computer, and reported receiving several spam emails, which the user did
not open Which of the following is MOST likely the cause of the reported issue?
A. There was a drive-by download of malware
B. The user installed a cryptominer
C. The OS was corrupted
D. There was malicious code on the USB drive
Correct Answer: D
Get the latest and complete CompTIA Security+ exam materials! Help you pass the first exam successfully! Click here to learn more…
Thank you for reading! I have told you how to successfully pass the CompTIA SY0-601 exam.
You can choose: https://www.leads4pass.com/sy0-601.html to directly enter the SY0-601 Exam dumps channel! Get the key to successfully pass the exam!
Wish you happiness!
ps.
Get free CompTIA SY0-601 exam PDF online: https://drive.google.com/file/d/1TkG4_k1sNDRwDR2x5XXVZcBoAqU-u5hF/